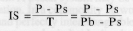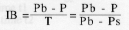Pricing Network Usage: A Market for Bandwidth or Market for Communication?
Skip other details (including permanent urls, DOI, citation information): This work is protected by copyright and may be linked to without seeking permission. Permission must be received for subsequent distribution in print or electronically. Please contact [email protected] for more information.
For more information, read Michigan Publishing's access and usage policy.
Presented at MIT Workshop on Internet Economics March 1995
Abstract
[1] A congestion pricing scheme will generate revenue only if demand for bandwidth at zero price exceeds the bandwidth capacity. The recipient of congestion pricing revenue has an incentive to cause congestion in order to collect more revenue. Congestion can be caused by withholding capacity, which on the Internet, can be achieved [a] by strategically not building capacity, or [b] by hiding capacity from routers by deliberate non-advertisement of routes or by route blocking, or [c] by self dealing whereby the owner of capacity buys back a portion of her own capacity. Such a strategy of withholding capacity is analogous to the monopolist's strategy of choosing an output quantity smaller than that which corresponds to marginal cost intersecting the consumers' demand curve. There are several means to discourage the monopolistic inefficiencies due to the withholding of capacity: [a] by making congestion pricing a revenue neutral process by giving displaced users or their proxies the congestion fees, or [b] by making users joint owners of the bandwidth resource and thus joint claimants to the congestion revenue, or [c] by assessing both an access fee and a congestion fee (i.e., a two part tariff), or [d] by having competition for bandwidth provision.
[2] Incidence and liability for communication (network usage) costs are two distinct issues. The liability for communication costs (obligation to collect and submit the communication cost) may be imposed by the network owner on senders (sellers of information) and/or on receivers (buyers of information). Different liability allocations will result in different compliance (accounting, collection, and verification) costs. The liability should be imposed so as to minimize such compliance costs.
The incidence of the communication cost (the manner in which the communication cost is shared between buyer and seller) is not a design choice: it is endogenous and depends only on the preferences of network users.
[3] The question of how the market for communication (e.g., bandwidth) and the market for information (e.g., files) are linked is addressed by exploring analogies with other network environments.
1. Introduction and Outline
This paper examines proposed congestion pricing schemes allocating traffic on the Internet [such as Varian, 1994a, or Cocchi et al, 1992]. In some cases, it is suitable to consider the task to be allocation of communication resources, i. e. a market for bandwidth. In other cases, it is beneficial to consider the task to be simultaneous allocation of both rights to information which can be sent over the Internet and the resources to be used for transmission, i. e. a joint market for information and for bandwidth. I will call this combination of information and bandwidth, communication. The formulation as a market for bandwidth ignores what it is that users want to send through the Internet; bandwidth is the only good considered, and can be considered solely from a sender's perspective. Both the formulation as a joint market for information and bandwidth and the formulation as a market for bandwidth alone addresses the possibility that both the sender and the receiver have a preference for the receiver receiving information.
The Internet and its predecessors (the Department of Defense's ARPAnet and the NSF's NSFNET) were funded by Federal government agencies, namely the Department of Defense and the National Science Foundation; individual users have not been charged for their use of networks, and have not generally been aware of the impact of their use on network performance. The number of people 'on the Internet' is reported to have grown at a rate of 10 percent per month since 1990 when Commercial Internet Exchanges (CIX) were first connected to the Internet to allow commercial traffic. Rapid growth in the number of users, the proliferation of online graphic images, and especially the one button click-to-download interfaces are factors that are increasing the demand for transmission capacity hence increasing the opportunity cost of misallocating transmission capacity. The phasing out of Federal government funding of Internet operation in the United States necessitates some form of alternative funding, such as revenue from fee for service operation.
The motivation for imposing a pricing scheme is to give users knowledge about the value of what they do to other people, and an interest to act so as to reduce harm done to others. It is assumed that the system which grants users the power to cause congestion also provides users the power to reduce congestion and thereby avoid needless or inefficient harm. A generous user who is willing to use a system after hours needs to know when after hours actually occurs. A less socially benevolent user, if offered a discount for after hours usage, may reschedule her use, not out of charity or of concern for the public good, but because it is in her interest to save money. Finally, a user must have sufficient power over the system so that after having decided to save money by using resources when they are cheap, the actions taken have that result. A user who submits her contributions to a mailing list at night will not have any benevolent impact if her software accumulates mail until 9 am and then transmits her messages.
A potential pitfall of introducing a pricing scheme is that it is not only the behavior of the consumers that may be affected, but also the behavior of the providers. Profit seeking providers will have as much knowledge, interest, and power in the system as any consumer.
This paper has three objectives. The first objective is to characterize congestion pricing as part of an optimal pricing scheme for network usage. The charge to users can in principle be based on any observable characteristic of or behavior by the user. Suitable behavioral characteristics on which to base a pricing scheme include [a] access; [b] capacity; [c] usage; and [d] priority of service. Observable non-behavioral characteristics include factors such as whether the user is a non-profit or for-profit institution, and the age of an individual user. Non-behavioral characteristics such as these could be used in setting prices, for example, by giving discounts to senior citizens or to nonprofit institutions. Somewhat equivalently, lump sums or rebates could be given to particular classes of consumers, who would then face the same price as everyone else in a uniform price market. Such schemes of non-behavior based price discrimination will not be considered in the present paper.
The access and capacity charges do not depend on if or how much the user uses the system, so these two charges can be combined into one lump sum charge for each user called the fixed charge, π. The usage and the priority charges depend on how and how much the user uses the system, and can be combined into one charge called the variable charge, p. Together, the fixed charge, π, and the variable charge, p, are a two-part tariff. If only one part of a multi-part tariff, the usage charge, is considered in isolation, an incentive appears to set the remaining part higher. For example, if p was reduced to 0 as a simplification of the analysis, the optimal value of π becomes larger. Therefore we model both the fixed charge and the variable charge simultaneously.
Secondly, the question of incidence and liability for communication (network usage) costs are two distinct issues. The liability for communication costs (obligation to collect and submit the communication cost) may be imposed by the network owner on senders (sellers of information) and/or on receivers (buyers of information). Different liability allocations will result in different compliance (accounting, collection, and verification) costs. The liability should be imposed so as to minimize such compliance costs. Third, and lastly, many people see analogies between the Internet and the Interstate highway system, as suggested by the nickname, "the Information Superhighway," and as demonstrated by the use of extended metaphors such as on-ramps, road kill and speed bumps. Fiber optic links are called pipes; and analysis of the Internet lends itself to many analogies with other network resources. The specific characteristics of various networks that make them similar or dissimilar to the Internet is explored.
2. The Multi-Part Tariff: Access, Capacity, Usage, and Congestion
The short run costs of operating the Internet backbone are all either sunk because they are due to past decisions or are fixed because they do not depend on the quantity of information sent. Here the short run is defined as the duration of time from present until just before new capital goods can be bought and installed. Such sunk and fixed costs include the construction and configuration of lines, switches, and routers, or the leasing of such assets. Once such costs have been incurred, the cost to the owner of these assets of providing an additional unit of bandwidth is zero, as long as the total bandwidth used is between zero and the capacity of the system. Additional usage, beyond the capacity of the present system, is impossible during the short run because we adopt a literal meaning for the term "capacity" and because of how we define the short run.
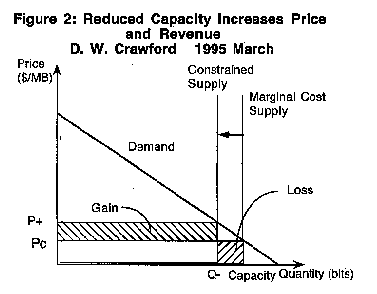
A congestion pricing scheme will generate congestion revenue only if there is congestion, i. e. if demand for bandwidth at zero price exceeds the bandwidth capacity. In Figure 1, for the smaller supply, the price for which quantity demanded is equal to quantity supplied is positive; but for the larger supply, a zero price allows all demand to be met. If the only revenue generated by a communication resource is that due to congestion pricing, the owner of the resource has a strong incentive to increase her revenue by causing congestion by, for example, withholding capacity. In Figure 2. the gain in revenue due to a higher per unit price more than offsets the loss in revenue due to fewer units of bandwidth sold; thus the supplier will keep reducing the quantity of bandwidth offered to the market until reaching the quantity where marginal revenue equals marginal cost (or zero). At this point the revenue gain due to a higher price per unit is just equal to the revenue loss due to selling one fewer unit. See Figure 3.
On the Internet, withholding capacity can be achieved by strategically not building capacity—by hiding capacity from routers. Analogously, one could cause congestion in a road network by hiring a few cars and drivers and having them feign breakdowns in strategic locations. On the Internet, we may cause congestion by what we may call demand pseudo augmentation whereby the apparent demand is increased by some form of supplier self-dealing. The optimal increase in demand shown in Figure 4 results in the same quantity legitimately consumed as does the optimal decrease in supply shown in Figure 3. By contrast, one could cause congestion in a road network by hiring many cars and drivers. But unlike cars, the packets that travel on the Internet are essentially free to generate and to dispose of. The demand could be augmented legitimately by providing access to more users or greater advertising of the benefits of Internet use. The pseudo-augmentation is due to the supplier of the bandwidth, or her collaborator, buying bandwidth solely to drive up the price. The collaborator would be refunded the entire cost of units purchased, so there is no net cost to the collaborator. Such a long run scheme would work easily on the Internet since it is costless to generate and request transmission of huge files (or many packets) and costless to discard these huge files (or many packets) upon receipt. In the financial world, self dealing whereby the owner of securities buys back a portion of her own holdings in order to manipulate the apparent market price is generally illegal. Such a scheme for raising the price up by pseudo-augmenting demand would not work in most other contexts, because there is a real cost of generating the articles sold or transmitted, and there is a further cost of then storing or disposing of them after their arrival at their destination.
Of the various strategies to reduce the quantity actually delivered to consumers in the market, the strategy of under investing in capital by under building capacity is the most attractive steady state solution, because presumably the smallest system is the cheapest system to build and yet it yields the same revenue as the other strategies. However, the notion of steady state in the Internet or computer industry is not appealing because both demand and technology continue to advance rapidly.
The strategy to build capacity and mask it out is appealing, because it accommodates growth in demand, and as less capacity is masked out, the supplier can claim credit for innovation and efficiency. Such a scenario is similar to that of an environmental engineer, who faced with a mandate to reduce emissions by half, declares, "This is the benchmark setting period - let's run dirty today". The strategy of pseudo-augmenting demand is less appealing, because the growth of total official quantity consumed will be under reported, and will hide the growth of the bandwidth providing company. Note that it is redundant to withhold capacity that has not been built.
There are several means to discourage the monopolistic inefficiencies due to the withholding of capacity:
[a] Revenue Neutral Congestion Pricing
Rather than allowing the network owner to keep congestion pricing revenue, the revenue could be given to displaced users. This is called a revenue neutral process because the revenue is collected from and given to the users, so the network owner is unaffected. This procure is similar to the practice of compensating passengers who are bumped from an overbooked airplane; it would be identical if the non-bumped passengers were taxed to pay for the bumping compensation. If the ticket prices were set with the possibility of bumping compensation in mind, then the situations are perfectly analogous. Such a system needs to block further entry by consumers once it is recognized that the system is overbooked or congested. The revenue neutral congestion pricing rule removes the interest the network owner has in having network congestion occur.
[b] Unitizing the Network
A system of managing a public good is for all the users to form a cooperative. The revenue from operation is divided among the users according to some agreed upon formula. Such an institution has been used extensively for managing oil reserves and aquifers with multiple well owners drawing from the same source [Libecap, 1989]. The unitized network curtails the incentive to cause congestion because it is the same agents who both sufferer of congestion and are claimants to congestion pricing revenue.
[c] Multi-Part Tariff
The charge to users can in principle be based on any observable characteristic of or behavior by the user. Suitable behavioral characteristics on which to base prices include:
- access (whether the user is in fact connected to the system);
- capacity (the maximum rate at which a user can move information through the system, whether or not the user actually has used the capacity—essentially this is a standby charge for having the option to use available capacity);
- usage (a charge for the actual quantity of information sent through the system); and
- priority (a charge for displacing other users in the event of congestion).
Observable non-behavioral characteristics include whether the user is a non-profit or for-profit institution, or the age of an individual user. Non-behavioral characteristics such as these could be used in setting prices, for example, by giving discounts to senior citizens or to non-profit institutions. Somewhat equivalently, lump sum or rebates could be given to particular classes of consumers, who would then face a uniform price market. Such schemes of price discrimination will not be considered in the present paper.
The access and capacity charges do not depend on if or how much the user uses the system, so these two charges can be combined into one lump sum charge for every user, called the fixed charge, π. The use and the priority charges depend on how and how much the user uses the system, so these charges are variable. The usage and priority charges can be combined into one charge, called the variable charge, p. Together, the fixed charge, π, and the variable charge, p, are a two-part tariff. The optimal solution for the network owner is to set π equal to the consumer's surplus (See Figure 1), and to set p equal to the marginal cost. The marginal cost is equal to the highest value that any displaced user put upon not being displaced. In an economically efficient allocation, the highest value that any displaced user put upon not being displaced is bounded by the lowest value a non-displaced user put on not being displaced. If there is no congestion, no user is displaced, and the marginal cost is zero. If there is congestion, and the buyers bid for usage, the marginal cost is equal to the highest rejected bid. If there is no congestion, no bids are rejected and the marginal cost is zero. The two part tariff so implemented is efficient because it provides the same quantity of the good as a competitive market would. The strategy of using a two-part tariff is normatively appealing because users pay a fixed fee based on their scale, so large sites pay more than small sites, and the variable fees vary with usage; however once packets are admitted to the system, each packet is routed alike, and all originator sites are treated alike.
The difficulty with the two part tariff approach lies in the fact that all consumers do not have the same individual demands, and thus have different consumer's surpluses. This difficulty could be overcome if the supplier could identify consumers with high demand and justify charging them a higher price and prevent resale by consumers given low prices to consumers given high prices. Since the proposed system has elicited bids for service, those bidding relatively high amounts can be presumed to be those with a high demand. The fact that such consumers have less chance of having their service interrupted helps to justify charging them a higher fee [Wilson, 1989]. If low bidding customers engage in resale, they will require larger capacity connections, and may need to bid higher in order to obtain the additional bandwidth. In doing so, they will have revealed themselves to have the higher demand of those to whom they would resell. Clearly, the opportunities for arbitrage in such a system are rather limited. If only one part, the variable charge, is considered in isolation, there appears an incentive for the supplier to withhold capacity. Therefore both the access charge and the congestion charge should be modeled simultaneously.
[d] Competition for Bandwidth Provision
Assuming compatibility and interoperability problems could be overcome, having multiple suppliers would compete away the monopolistic profits. If one supplier withheld bandwidth, another would be willing to provide it.
3. Incidence and Liability for Transmission Costs
The cost of communication (network usage, transportation of information), T, if any, can be modeled as a difference between the price the buyer pays for the information, Pb, and the price the seller receives for the information, Ps, so
Pb - Ps = T
The liability refers to the obligation to submit T to the transport provider. The incidence of a tax refers to the change in prices from a datum in a tax free market where the price for everybody was P. The buyers may see their price increase by (Pb - P) and the sellers see their price decrease by (P - Ps) upon imposition of a tax T.
Seller incidence IS refers to the portion of the tax paid by the seller:
Buyer incidence IB refers to the portion of the tax paid by the buyer:
Note that IS + IB = 1 is an identity.
Collecting a sales tax in a retail industry is analogous to collecting a communication fee. In the retail industry, where buyers greatly outnumber sellers, and sellers are less mobile than buyers, it is presumed more efficient to hold sellers liable for the tax; this division of labor reduces the number of agents to be monitored for compliance and evasion.
In the Internet context, providers of files (e. g., ftp archives or www sites) already assume the costs for disk space, access and capacity costs, and file maintenance. In some cases, such as files offered to provide technical support or advertising, the provider would be willing to incur the additional cost or transportation. In other cases, such as the distribution of shareware or non-commercial documents, the consumer would be willing to pay an additional cost. In either case, the file is made available and the buyer pays Pt and the seller keeps Ps. Implementing this system as a seller liable system would be easy, since the seller is the sender of the files; this may require (depending on incidence) having the seller collect a charge from the buyer. Implementing this system as a buyer liable system would require a charge back accounting system, in which the file sent by the seller has its transportation cost billed to by the buyer. The buyer-liable system has a greater security related obstacle in verifying that the buyers actually requested the files they receive and for which they are liable for transportation costs. An explicit hybrid liability scheme is also possible. In the hybrid liability scheme, the buyer and seller agree to some allocation of the transmission costs. For example, the buyer may agree to pay one dollar and the seller agree to pay the remainder of the transmission charge. Any system that bills the receiver for transmission cost will be easier to implement if the receiver is already paying for the content. It is assumed that there will be more cases of receivers paying senders to send files than senders paying receivers to receive files, thus most file transfer transactions would be file senders collecting money from file receivers. In these cases, it seems suitable for the sender to collect additional money to cover the receiver's incidence of transmission cost. Assuming that most file transactions are of the paying to receive mode and not the paying to send mode, a sender liable system seems likely to minimize the transactions costs. A COD or postage due type of system is not likely feasible, because of the storage requirement needed from the time the message is sent to the time the potential recipient is informed of incoming information and announces a willingness to pay or not.
4. How are networks similar or different?
A network is a set of nodes and arcs; each arc links two nodes. The use or function of a network is to allow some object to be sent from one node to another node. An arc may be directional, which implies that the sending is possible in only one direction. There may be more than one arc linking two nodes. The object transported may be water, oil or gas in the case of pipeline networks; or planes, trains and automobiles in the cases of airline, rail, and road networks, respectively. The planes, trains and automobiles hierarchically include people and freight as objects transported. In the case of information networks, such as computer data or telephone networks, the object transported is a bundle of information. A postal system may be considered a network; objects sent via mail may be considered information. In a commodity network (oil, gas, water, or electricity), the objects transmitted are generic and perfectly interchangeable. In an information network (mail, phone, computer data), the objects sent may be individualized and not interchangeable.
Example 1. Water transport network technology
- input: x = water at node A at time t1
- output: y = water at node B at time t2
- production function: f(x,t) = y
Note that in the water network example above, both the input and the output are time stamped. If t1 t2 then the flow is from A to B. Generally network flows are reversible, so it is important to keep track of the direction of flows and the time at which an object is at a particular node. A factor common to all types of networks is that their capacity to produce is not storable, so capacity unused today cannot be saved for use tomorrow. Note that the storage of capacity of a network to transmit is distinct from the storage of objects transported over the network. So for example, if a milkman takes one day off and does not use his capacity to deliver milk for a day, his capacity to deliver milk is not stored and accumulated, giving him double capacity on the following day. However, the undelivered milk may be stored.
The possible uses of a network literally maps from departure space (where you start) to arrival space (hopefully where you want to go). The example above was an example of a transportation activity. The network can formally be expressed as the set of all possible transportation activities. For example, a postal network can be represented as a mapping from and to the space generated by the Cartesian product of all possible pieces of mail, all possible locations of mail, and all possible instants of time. Of course, this may not be the most parsimonious representation. For a communication network, we may be able to think of discrete pieces of information represented by flashes of light or voltage fluctuations on a wire, as mail trucks on a road or as packages inside the mail truck. Though computers can send data over phone lines by using modems, the term 'phone network' and 'computer data network' are not synonymous. The cost of operating a network typically depends on the amount of traffic it bears; the Internet is an exception. This phenomenon of more users causing greater operation cost is a negative externality. In the case of increased connectivity, having more users is a positive externality because more people are reachable.
Comparison of Networks
[a] Net Flow vs. Total Flow
The commodity networks do share a common property that one unit transferred from node B to node A is a perfect substitute for a unit that already was at node A. Non-commodity transportation networks (planes, trains, and automobiles) do not share this perfect substitution regardless of origin property. In communication, each unit of information has a source node (author) and receiver node (reader). Receiving mail or phone calls intended for another node is typically useless (unless it's cash in the mail) both for the sender and recipient. In communication, there are intermediate cases such as broadcasting, in which watching the State of the Union Address delivered on station 2 is a perfect substitute for watching the State of the Union Address delivered on station 3.
Table 1. Network Type vs. Characteristics
| Network Type | Characteristic | ||||
| Store and Forward | Net Flow or Total Flow | Frictional loss | Self Powering | Measure of Capacity | |
| yes | total | possible | no | letters/day | |
| electricity | no | net | yes | yes | power (MW) |
| data | maybe | total | maybe | NA | bits per second |
| telephone | no | total | no | NA | calls |
| road | yes | total | possible | yes/NA | trucks per hour |
| water | yes | net | yes | no | kg per second |
| gas/oil | yes | net | yes | possible | kg per second |
In commodity flow networks (electricity, oil, gas, water), only net transfers between two nodes during a period or net transfer rates at a time matter. In information networks (data, mail), the total number of objects transferred between nodes matters. Compare the following three cases.
Example 2. Suppose we are currently pumping 50 units of water from node A to node B. The net transfer between nodes is 50 units from node A to node B.
Example 3. Suppose we are currently pumping 80 units of water from node A to node B and simultaneously pumping 30 units of water through the same pipe from node B to node A. The net transfer between nodes is 50 units from node A to node B.
Both of these examples [2 and 3] describe the same net flow of water. Example 3 may appear to be an inefficient use of the network, but since our consideration will be in terms of net flows, and the second case is identical to the first case in terms of net flow, the second case is as efficient as the first case.
[b] Frictional losses
In a pipeline network, such as one containing water, gas, or oil, flow is induced by increasing pressure at source nodes and/or decreasing pressure at sink nodes. In electric networks, flow is induced by increasing voltage at source nodes and/or decreasing voltage at sink nodes. Gas and oil networks have frictional losses, and pumps may be used to overcome such losses, but it is not necessarily gas used to power pumps in a gas network to overcome friction or oil powered pumps used in an oil network. An electric network has losses that are analogous to friction: the resistance/impedance of the wires. In an electric network it is the electricity itself that is used up to overcome this resistance. The electricity used up in an electric network is like milk drunk by a milkman who drinks more milk the longer and more tiring his route. A water network arc thus has a property known as conservation of mass, where water going in one end comes out the other. But an electric network has in kind losses, so what comes out at one end is less than what went in at the other end. These in kind losses make modeling the electric network more difficult than modeling a network that conserves mass. Communication networks are externally powered. For example, the mailman provides the energy to sort and move mail; the mail itself is not energized. But we may think of the bandwidth used to carry header data as frictional loss encountered when sending a data payload.
[c] Store and Forward
Above it was stated that all networks share a property that their capacity is not storable. However, the good transmitted on a network may be storable. For instance, a mailbox is a node in a mail network. The mailbox sends (is emptied) once or twice a day, but may receive incoming mail hundreds of times per day. Between events of being emptied, the mailbox is storing mail. Nodes on gas, water, or oil may have reservoirs for storing product between two other nodes. Many data networks have a store and forward architecture. However, electricity itself is not storable, so nodes in an electric network cannot be used for storage. As a low level protocol, Internet does not store and forward, but applications such as Usenet do store and forward.
[d] Measuring Capacity
Gas and oil may be measured by mass, number of molecules, or volume at some pressure and temperature, or energy content at some pressure and temperature. Electricity is measured in terms of energy.
Quantifying communication is more problematic than quantifying electricity or water. Suppose you wish to tell someone which horse you think will win a race against seven other horses. You might transmit the DNA genetic code of the winning horse; that would be a lot of information. If the horses have proper and unique English names, you may transmit the name of the horse, 'Sir Ed, 3rd'. If the horses have numbers, you may transmit, '1'. That is very little information, but in this context, '1' is just as sufficient to identify the horse as is providing the complete genetic code. In this example, we need to indicate one of eight possible states of the world, since there are eight horses. If we start with a set of eight horses and make three binary decisions, we will have uniquely identified a particular horse. If each horse has a unique indicator, then by making three binary decisions, we will have uniquely identified a particular indicator, and by the uniqueness of the indicator, we will have identified a particular horse. The lesson here is that we can measure information as the number of binary decisions needed to get from some set of possible states of the world that are common knowledge to the knowledge that one particular state of the world is true. In the eight horse race, the amount of information needed to identify a particular horse is three binary decisions, or three bits.
To write a letter on a computer, we commonly use an extension of the roman alphabet called ASCII, which has 128 characters (a,...,z, A,...,Z, 0,...9, and punctuation), or a PostScript alphabet which may have up to 220 characters. Newer alphabets are much larger: Apple Computer's QuickDraw GX alphabet has 65,000 possible characters [Arnold]. An ancient computer might have used an alphabet of 38 characters (A,..,Z, 0,...,9,., ,) and therefore needs 6 bits per character of English (38 26 = 64). A modern computer which is using display PostScript with a character set of 220 needs 8 bits per character (220 28 = 256). These example show why saving the same content as different file types may result in different file sizes. The trend towards much larger symbol sets allows much more richly formatted text, but at a cost of longer files. A more detailed discussion of measuring information can be found in [Cover].
This analysis is germane to Internet pricing, because unitized systems (see Section 2b) such as America Online have been designed to send graphical icons once and save them locally; then subsequent invocations to the icon need pass only a cryptic abbreviated reference to the icon, not the icon itself. However, the user who has stored the icon gets to see the icon, and not the cryptic reference.
The World Wide Web system is not organized to store icons with common identifiers, but does have a system called Hyper Text Markup Language (HTML) that allows for very abbreviated formatting commands to be sent, such as em emphasis /em which sends the word emphasis with information that the recipient's system should emphasize the word using boldface, or italics, as determined by the recipient's system. HTML does not tell the recipient's system how to render boldface or italic text; that is already known to the local system.
Conclusion
For analysis of the incidence of transmission costs on senders and receivers of information, it is best to consider the task to be allocation of both bandwidth and rights to information. For analysis of congestion pricing, the content can be ignored, but the access and capacity charges must be considered jointly with the usage and priority charges.
Acknowledgments
I would like to thank Stephen J. Rassenti, Vernon L. Smith, John Hawkinson, Dale O. Stahl and participants in the experimental economics workshop at the University of Arizona for useful comments and suggestions. Remaining misconceptions and errors are the fault of the author.
Author Information
David W. Crawford ([email protected]) is a doctoral student in the Department of Economics at the University of Arizona. He can be reached at: McClelland Hall 401; University of Arizona; Tucson, AZ 85721; 520-621-6224.
References
Arnold, Kandy. "GX will provide printing power", MacWeek, 1994 August 15.
Bellamy, John. Digital Telephony. New York: John Wiley and Sons, 1991. Bergseth, F. R. and S. S. Venkata. Introduction to Electric Energy Devices, Englewood Cliffs, New Jersey, 1987. 370 pp.
Cocchi, R., Estrin, D., Shenker, S., and Zhang, L. "A study of priority pricing in multiple service class networks". In Proceedings of Sigcomm '91. (1991). Available from: ftp://parcftp.xerox.com/pub/net-research/pricing1.ps.Z
Cocchi, R., Estrin, D., Shenker, S., and Zhang, L. "Pricing in computer networks: Motivation, formulation, and example". Technical Report, University of Southern California. (1992).
Cover, Thomas M. and Joy A. Thomas. Elements of Information Theory. New York: John Wiley and Sons, Inc. 1991.
Fudenberg, Drew and Jean Tirole. Game Theory. Cambridge, Mass.; MIT Press, 1992.
Kahn, Robert E. "The Role of the Government in the Evolution of the Internet", ACM Communications ,Vol. 37, No. 8 (1994), pp 15-19. [doi: 10.1145/179606.179729]
Laffont, Jean-Jacques and Jean Tirole. A Theory of Incentives in Procurement and Regulation. Cambridge, MA: MIT Press, 1993.
Libecap, Gary D. Contracting for Property Rights. Cambridge [England]; New York: Cambridge University Press, 1989.
MacKie-Mason, J. K., and Varian, H. (1993). "Some Economics of the Internet". Technical Report, University of Michigan.
MacKie-Mason, J. K., and Varian, H. (1994a). "Pricing the Internet". In Kahin, B., and Keller, J. (Eds.), Public Access to the Internet. Unknown.
MacKie-Mason, J. K., and Varian, H., (1994b) "Economic FAQs About the Internet", Journal of Economic Perspectives, (Fall, 1994) anonymous ftp, gopher, or World Wide Web at gopher.econ.lsa.umich.edu. Version: April 4, 1994. [Ed note: this link no longer active. Try accessing the Journal of Electronic Publishing version above.
Mas-Collel, Andreu. The Theory of General Equilibrium: A Differentiable Approach. Cambridge University Press, 1985.
Rassenti, Stephen, S. S. Reynolds, V. L. Smith. "Cotenancy and competition in a an experimental auction market for natural gas pipeline networks". Economic Theory, 3, (1993). pp. ??? ???.
Wilson, R. "Efficient and Competitive Rationing", Econometrica 57 (1989) pp. 1-40. [doi: 10.2307/1912571]